Don’t Forget The Updates
Just a couple quick updates, I can’t believe its already been three months since my last blog post. So much for the Gitlab CI spurring more frequent posts….
Playing With Honeypots
DShield Honeypot
A friend mentioned the DShield Honeypot project, which looks like a great way for anyone to contribute to cybersecurity research. DShield Honepot is optimized to sort of set it and forget it, and the device will become a sensor for the SANS Internet Storm Center. This is great for beginners, but I felt that it takes too much control from the operator. In my case, I would like to have more direct access to the logs of the adversarial activities, as well as isolating the malware itself to practice reversing.
Cowrie SSH/Telnet Honeypot
After digging around a bit, it looks like cowrie is just what I’m looking for. From their documentation:
What is Cowrie
Cowrie is a medium to high interaction SSH and Telnet honeypot designed to log brute force attacks and the shell interaction performed by the attacker. In medium interaction mode (shell) it emulates a UNIX system in Python, in high interaction mode (proxy) it functions as an SSH and telnet proxy to observe attacker behavior to another system.
Cowrie is maintained by Michel Oosterhof.
Documentation
The Documentation can be found here.
I deployed cowrie in medium interaction mode initially, and started receiving rogue login attempts within 10 minutes.
After about 12 hours I received my first malware sample!
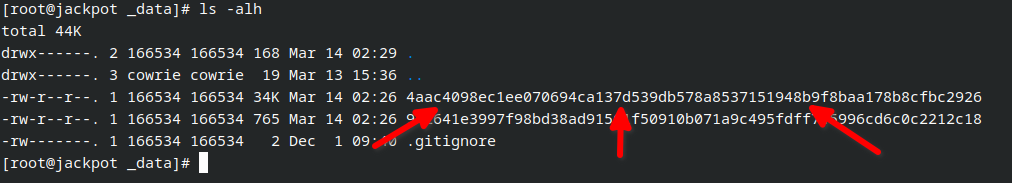
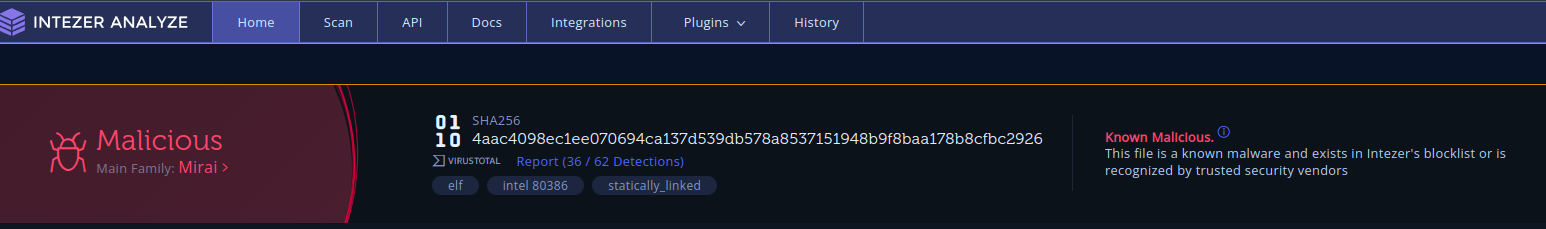
As such, the current plan is to deploy a VM factory backend for the honeypot to serve realistic environments to adversaries. I hope this will net more interesting and fresh malware to pick apart and analyze. To save on costs, I plan on using spare hardware for the VM factory. I will use either tailscale or nebula to provide a private mesh network between the cowrie instance running in the cloud at an undisclosed provider, and the VM factory running at a similarly undisclosed location.
I have been considering creating a guide for the particular configuration of cowrie that I am creating. I’m trying to improve my note-taking skills to enable this - I am so bad about stopping and capturing screenshots!
Mirroring Repositories… Eventually
I’ve begun the process of mirroring some of my gitlab repos to public hosts. I am probably going to use codeberg primarily for this, at least initially. Right now, most of my work is spread out between github and a private gitlab instance I run in house. I plan on moving away from github as time permits. Despite the large amount of functionality, some of their actions of late have been troubling, in my opinion. This, of course, means more work. The work requires time. Time seems to be increasingly scarce, these days!
Also this presents the issue of sanitizing some of my projects and making them suitable for use by others. I am used to building various application stacks for my own purposes, and I am excited about the challenge that this presents for me. For my first attempt, I have released an elastic stack with a caddy frontend, here. I am certain there are bugs. However, this could be an excellent testing tool, and introduction to the elastic stack. Please check it out and leave me some feedback? I know I am speaking to the void, but who knows maybe someone actually reads these! 😄
Still Job Hunting, Unfortunately
I am currently on mid-semester break, during my final semester for my BAS Cybersecurity program at SPC. The job hunt has been abysmal, to be honest. I am trying to remain positive, despite the previous statement! I am certain that I will find opportunity, eventually.
The company that takes a chance on me will undoubtedly profit from my passion and ability. Are you hiring for cyber security, Linux system administration, or DevOps roles? Feel free to reach out to me here!